Hashcat Masks Github . generates masks for hashcat using all the possible combinations specified in an array. Generate a list of hashcat masks from a wordlist. Here are 9 public repositories matching this topic. Most of what you're looking to do can be accomplished with the pack toolkit:. a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time. # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. generate hashcat masks from a password list. Instantly share code, notes, and snippets. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting.
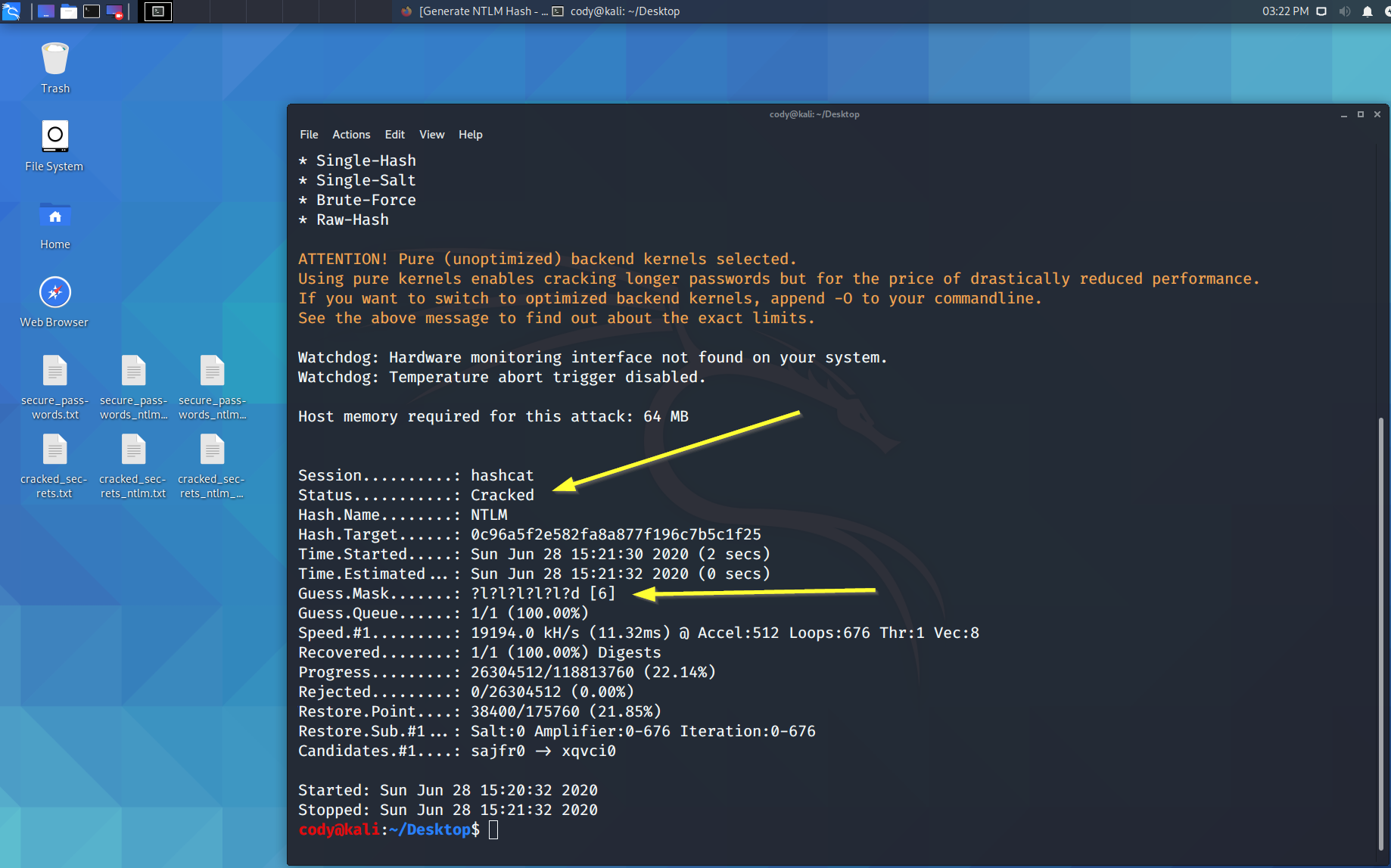
from blog.codyrichardson.io
generates masks for hashcat using all the possible combinations specified in an array. Here are 9 public repositories matching this topic. Generate a list of hashcat masks from a wordlist. generate hashcat masks from a password list. Instantly share code, notes, and snippets. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time. Most of what you're looking to do can be accomplished with the pack toolkit:.
Hashcat Cracking MD5 and NTLM Hashes
Hashcat Masks Github generate hashcat masks from a password list. generate hashcat masks from a password list. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. Most of what you're looking to do can be accomplished with the pack toolkit:. generates masks for hashcat using all the possible combinations specified in an array. Instantly share code, notes, and snippets. Generate a list of hashcat masks from a wordlist. # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. Here are 9 public repositories matching this topic. a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time.
From www.youtube.com
How To Install & Use Hashcat On Mac OSX YouTube Hashcat Masks Github Here are 9 public repositories matching this topic. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. generates masks for hashcat using all the possible combinations specified in an array. Most of what you're looking to do can be accomplished with the pack toolkit:. Instantly share code, notes, and snippets.. Hashcat Masks Github.
From github.com
mask attack slow · Issue 1522 · hashcat/hashcat · GitHub Hashcat Masks Github a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time. generate hashcat masks from a password list. generates masks for hashcat using all the possible combinations specified in an array. Most of what you're looking to do can be accomplished with the pack toolkit:. Generate a list of. Hashcat Masks Github.
From tbhaxor.com
Brute forcing Password with Hashcat Mask Method Hashcat Masks Github list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. generates masks for hashcat using all the possible combinations specified in an array. Generate a list of hashcat masks from a wordlist. generate hashcat masks from a password list. a set of prioritized hashcat masks intelligently developed from terabytes. Hashcat Masks Github.
From hack543.com
深入 hashcat 系列:Mask Attack Mode Hack543 Hashcat Masks Github generate hashcat masks from a password list. Most of what you're looking to do can be accomplished with the pack toolkit:. generates masks for hashcat using all the possible combinations specified in an array. # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. a. Hashcat Masks Github.
From hackware.ru
Использование файлов масок .hcmask в Hashcat для максимально гибкой Hashcat Masks Github # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. generates masks for hashcat using all the possible combinations specified in an array. Generate a list of hashcat masks from a wordlist. Instantly share code, notes, and snippets. a set of prioritized hashcat masks intelligently developed. Hashcat Masks Github.
From github.com
GitHub NSAKEY/nsarules Password cracking rules and masks for Hashcat Masks Github Here are 9 public repositories matching this topic. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. Most of what you're looking to do can be accomplished with the pack toolkit:. generate hashcat masks from a password list. Instantly share code, notes, and snippets. a set of prioritized hashcat. Hashcat Masks Github.
From blog.csdn.net
hashidentifier,hashcat的使用教程:_hashidentifier下载CSDN博客 Hashcat Masks Github Most of what you're looking to do can be accomplished with the pack toolkit:. generates masks for hashcat using all the possible combinations specified in an array. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. Generate a list of hashcat masks from a wordlist. Instantly share code, notes, and. Hashcat Masks Github.
From github.com
hash type 13100/krb5tgs mask mode yields no cracks · Issue 1512 Hashcat Masks Github # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. Generate a list of hashcat masks from a wordlist. Most of what you're looking to do can be accomplished with the pack toolkit:. generates masks for hashcat using all the possible combinations specified in an array. Here. Hashcat Masks Github.
From github.com
GitHub PortSwigger/hashcatmaskprocessor Hashcat Masks Github # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. generate hashcat masks from a password list. a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time. Here are 9 public repositories matching this topic. Most of. Hashcat Masks Github.
From github.com
Hashcat 4.1.0 Windows PATH Bug · Issue 1539 · hashcat/hashcat · GitHub Hashcat Masks Github Here are 9 public repositories matching this topic. Instantly share code, notes, and snippets. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. Generate a list of hashcat masks from a wordlist. # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending. Hashcat Masks Github.
From github.com
GitHub hspiit/maskukf Instance Segmentation Aided 6D Object Pose Hashcat Masks Github generate hashcat masks from a password list. Generate a list of hashcat masks from a wordlist. Instantly share code, notes, and snippets. generates masks for hashcat using all the possible combinations specified in an array. Most of what you're looking to do can be accomplished with the pack toolkit:. list of the top 5,000 masks created from. Hashcat Masks Github.
From github.com
Hashcat Integer overflow detected in keyspace of mask · Issue 2985 Hashcat Masks Github # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. Generate a list of hashcat masks from a wordlist. Most of what you're looking to do can be accomplished with the pack toolkit:. generate hashcat masks from a password list. generates masks for hashcat using all. Hashcat Masks Github.
From blog.codyrichardson.io
Hashcat Cracking MD5 and NTLM Hashes Hashcat Masks Github Most of what you're looking to do can be accomplished with the pack toolkit:. Instantly share code, notes, and snippets. a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time. generates masks for hashcat using all the possible combinations specified in an array. Generate a list of hashcat masks. Hashcat Masks Github.
From github.com
GitHub gobi/hashcat Hashcat Masks Github Instantly share code, notes, and snippets. generates masks for hashcat using all the possible combinations specified in an array. a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. generate. Hashcat Masks Github.
From www.youtube.com
Hashcat mask attack YouTube Hashcat Masks Github Here are 9 public repositories matching this topic. # then smart bruteforce using masks (custom charset can be usefull too) # can be quite long, depending on the mask. generates masks for hashcat using all the possible combinations specified in an array. Instantly share code, notes, and snippets. generate hashcat masks from a password list. Most of. Hashcat Masks Github.
From github.com
Metamask Token length exception · Issue 3429 · hashcat/hashcat · GitHub Hashcat Masks Github generate hashcat masks from a password list. generates masks for hashcat using all the possible combinations specified in an array. a set of prioritized hashcat masks intelligently developed from terabytes of password breach datasets and organized by run time. Generate a list of hashcat masks from a wordlist. # then smart bruteforce using masks (custom charset. Hashcat Masks Github.
From github.com
hashcatstyle wordlist mask feature not work · Issue 823 · owaspamass Hashcat Masks Github Instantly share code, notes, and snippets. Here are 9 public repositories matching this topic. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. generates masks for hashcat using all the possible combinations specified in an array. a set of prioritized hashcat masks intelligently developed from terabytes of password breach. Hashcat Masks Github.
From github.com
I am asking kindly to add a new bruteforcing mask feature developers of Hashcat Masks Github Here are 9 public repositories matching this topic. list of the top 5,000 masks created from all publicly available password dumps, with 9+ characters, meeting. generate hashcat masks from a password list. Most of what you're looking to do can be accomplished with the pack toolkit:. a set of prioritized hashcat masks intelligently developed from terabytes of. Hashcat Masks Github.